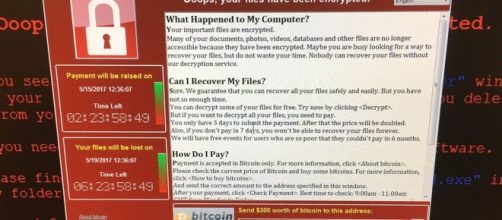
The owners of the 200,000 computers in 150 countries affected by the WannaCry Ransomware should not pay the $300 to $600 in Bitcoins being demanded by hackers. The former chief executive of the Internet Industry Association, Peter Coroneos, cited two reasons for not paying the amount asked by the hackers.
The first reason is a matter of principle which is to always say “no” so as not to perpetuate bad conduct. The second reason is the hackers could not be trusted with keeping their end of the deal. A Telstra cybersecurity report in 2017 found that one in three organizations in Australia hit by a previous ransomware attack did not recover their files despite paying the ransom.
Paying the ransom is a dubious choice
The report said 60 percent of organizations in Australia suffered from at least one malware attack in the last 12 months. Of the 60 percent, 57 percent paid the ransom, but only two in three gained access to their files again, The Guardian reported.
Coroneos said that paying the ransom is like rolling the dice and the victim’s chances are not good. It makes paying up a dubious choice because it does not come with a guarantee that the hacker will release the files and makes the victim a soft target since it boosts their chances of being attacked again in the future.
Malware attacks are random
For ransomware victims whose files were released after payment of the ransom, he said it should be used as an opportunity to consider boosting their cybersecurity practices as their top priority.
Coroneos admitted there are risks that come with not paying the ransom especially for computer owners who do not backup their files or have recovery strategies in place.
Another cyber Security expert, Trevor Long, EFTM.com.au technology commentator, noted that while attacks like the WannaCry Ransomware are common, hackers often do not have a specific business or person as a target because their approach is random. Most victims are the unlucky ones who have the misfortune of clicking a malicious link or downloading an infected content.
Cyber security firms link malware with North Korean group
While some reports identified the hacker group Shadow Brokers as the culprit behind WanaCryptor 2.0’s spread, Reuters reported that Symantec Corp.
and Kaspersky Lab, cyber security companies, are looking into technical evidence and investigating if a North Korean hacking group is involved in Friday’s cyberattack.
Some codes in an older version of the WannaCryRansomware were also used before by the Lazarus Group, reportedly based in Pyongyang, which explains why the two companies are looking further into the connection of North Korea into the attack.