The current global ‘WannaCry’ ransomware attacks have inspired the introduction of a new bill in the House. The Protecting Our Ability to Counter Hacking (PATCH) Act was introduced on Wednesday and supported by Representatives Ted Lieu and Blake Farenthold, and Senators Brian Schatz, Ron Johnson and Cory Gardner. It would see the Department of Homeland Security chairing a Review Board to make sure that software vulnerability policies are consistently disclosed to non-government entities.
The PATCH Act
Currently, the government has the Vulnerabilities Equities Process or VEP in place on how to inform the technology industry of software problems that it discovered.
In practice, such information often did not make its way to the vendors in time for the software companies to come up with patches to remedy the exploits.
The PATCH Act will have the Review Board identify “whether, when, how, to whom, and to what degree” a vulnerability held by a government entity might be disclosed. Some industry groups and technology companies have been backing the act, including the Coalition for Cybersecurity Policy and Law, the Center for Democracy and Technology, McAfee and Mozilla, the developer of the Firefox browser.
ICYMI: Vulnerabilities Equities Process may be law with PATCH Act https://t.co/Xzbao0lp3J Thanks @jeremiahg @DenelleDixon @hitesh_vectra
— Michael Heller (@MT_Heller) May 19, 2017
Other members of the review board would be the secretary of Homeland Security, the secretary of Commerce, the director of National Intelligence, and the directors of the Federal Bureau of Investigation (FBI), the Central Intelligence Agency (CIA) and the director of the national security Agency (NSA), along with ad hoc members.
According to a statement about the bill, the bipartisan legislation would add transparency and accountability to the U.S. government, who is among the many parties researching zero-day vulnerabilities. Such information is not always made available to the vendors for national security purposes.
Last week’s global attacks
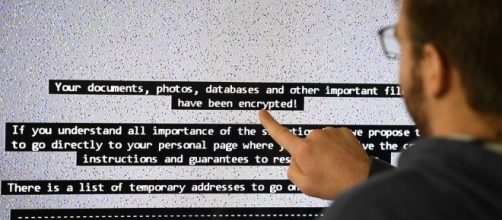
The WannaCry global ransomware was launched on May 12, infecting more than 230,000 computers in at least 150 countries. Microsoft has blamed the NSA for stockpiling cyber weapon, which is what the malware is said to be based on.
The ransomware meddled with trains in Germany, locked up access to UK’s National Health Service computers, banks, and schools, and further caused the shutdown of Renault factories in Europe.
The new analysis suggested that the ransomware, which holds computer files as a hostage, could have links to a North Korean group.
Once a computer is infected, a message will be displayed demanding that the user pays $300 to $600 in bitcoins for access. The U.S. government has largely blamed Russia and China for the events leading to the WannCry global outbreak.