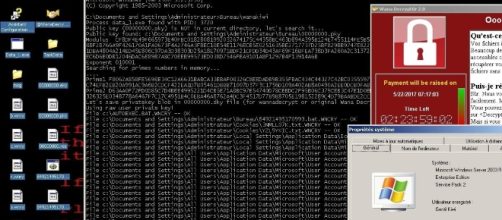
The owners of Windows XP computers infected with the ransomware 'WannaCry' virus could be able to decrypt the data without the need to pay the $ 300 redemption asked by the cyber criminals, thanks to a tool discovered by a French researcher.
According to an article published on the website thehackernews, Adrien Guinet, a cyber Security researcher for the French start-up Quarkslab, discovered a way to recover the secret encryption keys which were used by 'WannaCry'. This method works on Windows 7, Windows XP, Windows Server 2003 and 2008 and Windows Vista.
Description tool for the 'WannaCry' malware
The "WannaCry" encryption method works by generating some keys on the computer of the victim based on prime numbers — a public key, and a private key. These keys are used encrypt and decrypt the files from the system. In order to prevent the access of the victims to the private key, so they won't be able to decrypt the blocked files, "WannaCry" deletes the key from the system, leaving the victims no way to recover their files except to pay the redemption to the hacker.
But here is the secret — Guinet says "WannaCry "doesn't delete the prime numbers from the memory of the computer before releasing the associated memory. Based on this discovery, he released a decryption tool for the cyber attack called "WannaKey." This tool simply tries to recover from the memory the 2 prime numbers used to generate the encryption keys.
The decryption method has some limitations
However, the method has some limitations. It can work only if the infected computer was not restarted after it was infected and if the associated memory was not deleted by another process.
Guinet warns that the computer should not be restarted after being affected by the malware so this method could work. He also says it may not work in all cases.
'WanaKiwi' may be the solution to this type of malware
'WannaKey' can only extract the prime numbers from the affected computer's memory. This solution can only be used by the people who are able to use those prime numbers to manually generate the decryption key to decrypt their files. For this reason Benjamin Delpy, another cyber security researcher has developed another application called "WanaKiwi" which is easy to use.
This tool is based on Guinet's discovery and it makes the entire process of decrypting the infected files easier.
To use the 'WanaKiwi' tool the victims have to download it from Github and to run it on the infected computer by using the command line.
Matt Suiche from the security company Comae Technologies has confirmed that 'WanaKiwi' works on Windows 7, Windows Vista, Windows XP and Windows Server 2003 and 2008. Suiche also made a demonstration about how to use this tool to decrypt the files.